Who Am I?
Hello There ^_^ .
In few words. I’m Meshal AlMansour AlYami, A passionate RedTeam Operator who’s trying to improve his skills day by another. For me Cybersecurity isn’t just about a job or even an engagement to be done. It’s passion , happiness, enthusiasm, mentality and much more. Sometimes I wish my day was longer than 24hrs just to stay in front of my computer and do CyberSecurity stuff (Because simply this is the thing that I like). I believe that (The sky isn’t the limit for me. NOTHING IS). Scroll down to figure out some of my achievements that I’ve done within about 3 years of experience.
WORK EXPERIENCE:
- VAPT Consultant @ Cyberani since - (Oct, 2023)
- Building new services such as Source Code Review and Red Teaming services.
- Implementing penetration testing and vulnerability assessment automation tools and processes.
- Conducting web applications, network penetration tests for Cyberani Clients.
- Performing vulnerability assessments for Cyberani Clients.
- Organizing Cyberani CTF competitions for events such as LEAP
- Penetration Tester @ Ministry of Communications and Information Technology of Saudi Arabia (Feb, 2022 - Oct, 2023)
- Conducting web applications, network and mobile applications penetration tests
- Research, evaluate, document and discuss findings with responsible teams including but not limited to [ITsec, System, PMO, infrastructure and network teams]
- Following up and re-test(validate) any submitted reports in order to make sure that the countermeasures have been done properly.
- Completing Essential Cybersecurity Controls (ECC) PT requirments
- Simulating the adversary most recent attacks/techniques
- Research, evaluate, document and discuss findings with responsible teams including but not limited to [ITsec, System, PMO, infrastructure and network teams]
- Source Code Review
- Review and provide a feedback for some GRC requests from a PT/VA perspective.
- Keeping up to date with recent vulnerabilities and validate/report them to the responsible teams.
- PT Training for MCIT cybersecurity department trainees
- Penetration Tester @ Synack since (Synak RedTeam Member) - (Part Time)
- Conducting web applications white/black box tests
COURSES & CERTIFICATIONS:
- Offensive Security Web Expert (OSWE)
Offensive Security
- GIAC Exploit Researcher and Advanced Penetration Tester (GXPN)
SANS Institute
- Exploit Researcher and Advanced Penetration Tester (GXPN CTF Coin - 1st place)
SANS Institute
- Web Application Penetration Testing eXtreme (eWPTXv2)
eLearnSecurity
- Offensive Security Certified Professional (OSCP)
Offensive Security
- Web Application Penetration Testing (eWPT)
eLearnSecurity
- TOEFL iBT Test
ETS TOEFL (Score: 71)
CVEs
- CVE-2023-4059:
The function wppb_create_form_pages that’s being hooked to the admin_init action is accessible to un-authenticated end-users due to the lack of proper authorization checks which allow threat actors to create/publish [Register/Edit Profile/Log in]
CVE-2023-4059
- CVE-2021-3138:
Discourse 2.7.0 - Rate limit Bypass which leads to 2FA Bypass
CVE-2021-3138
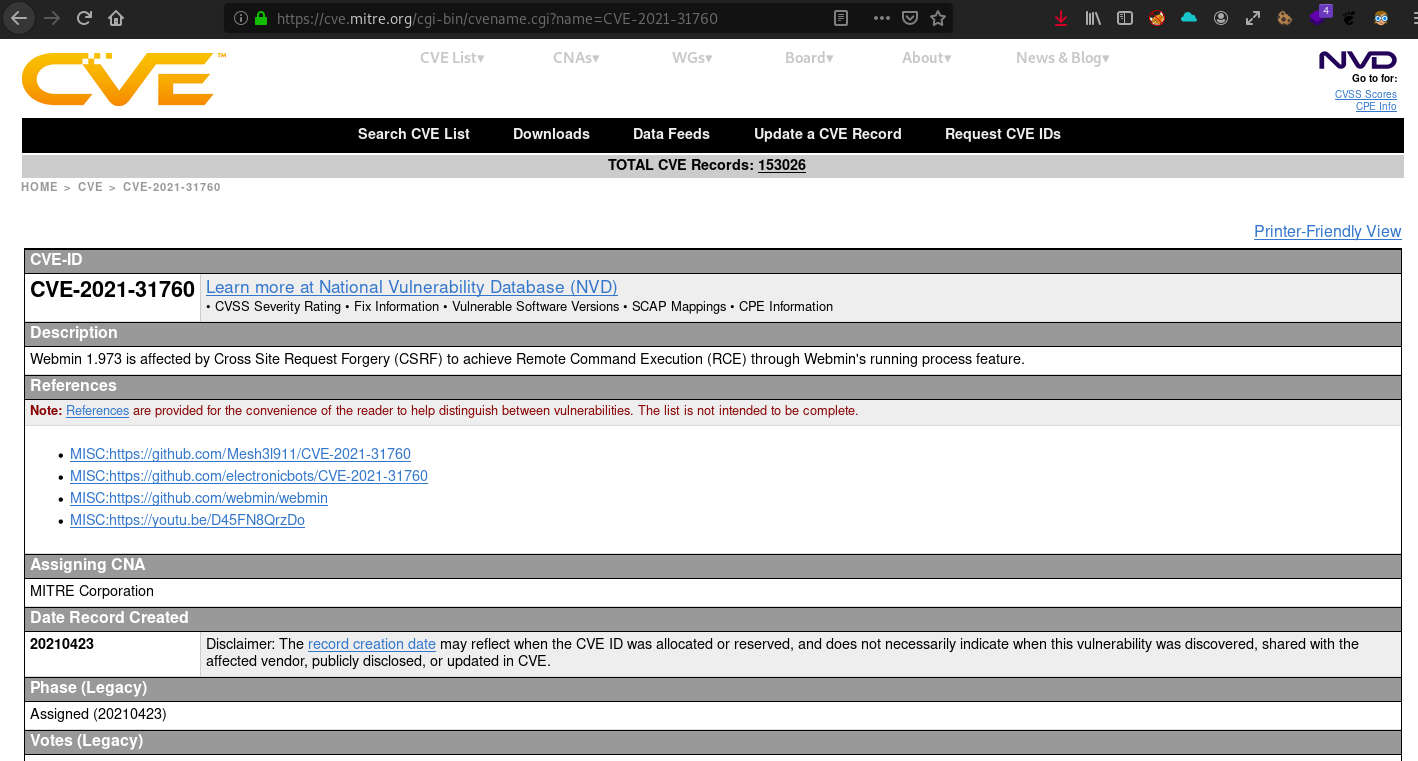
- CVE-2021-31760:
Webmin 1.973 - Exploiting a Cross-site request forgery (CSRF) attack to get a Remote Command Execution (RCE) through the Webmin's running process feature
CVE-2021-31760
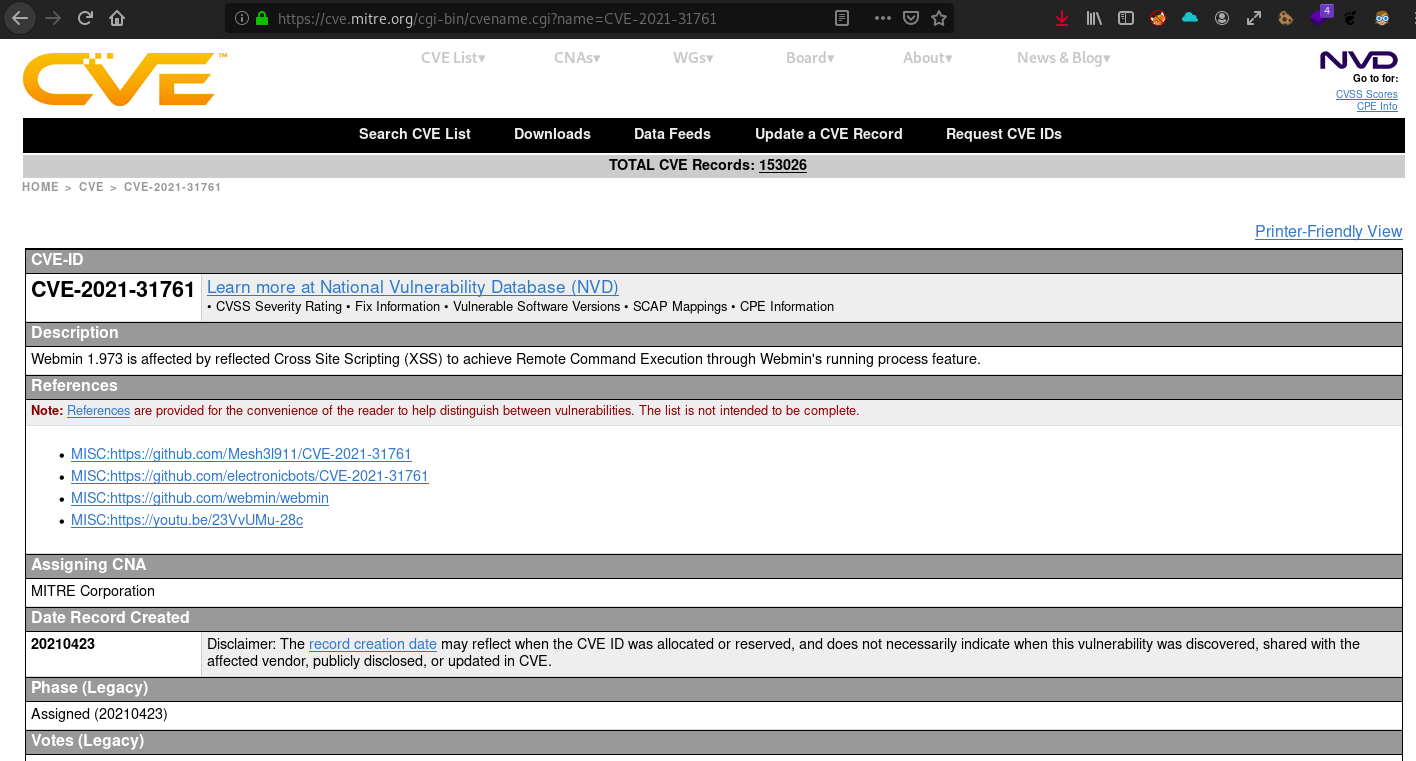
- CVE-2021-31761:
Webmin 1.973 - Exploiting a Reflected Cross-Site Scripting (XSS) attack to get a Remote Command Execution (RCE) through the Webmin's running process feature
CVE-2021-31761
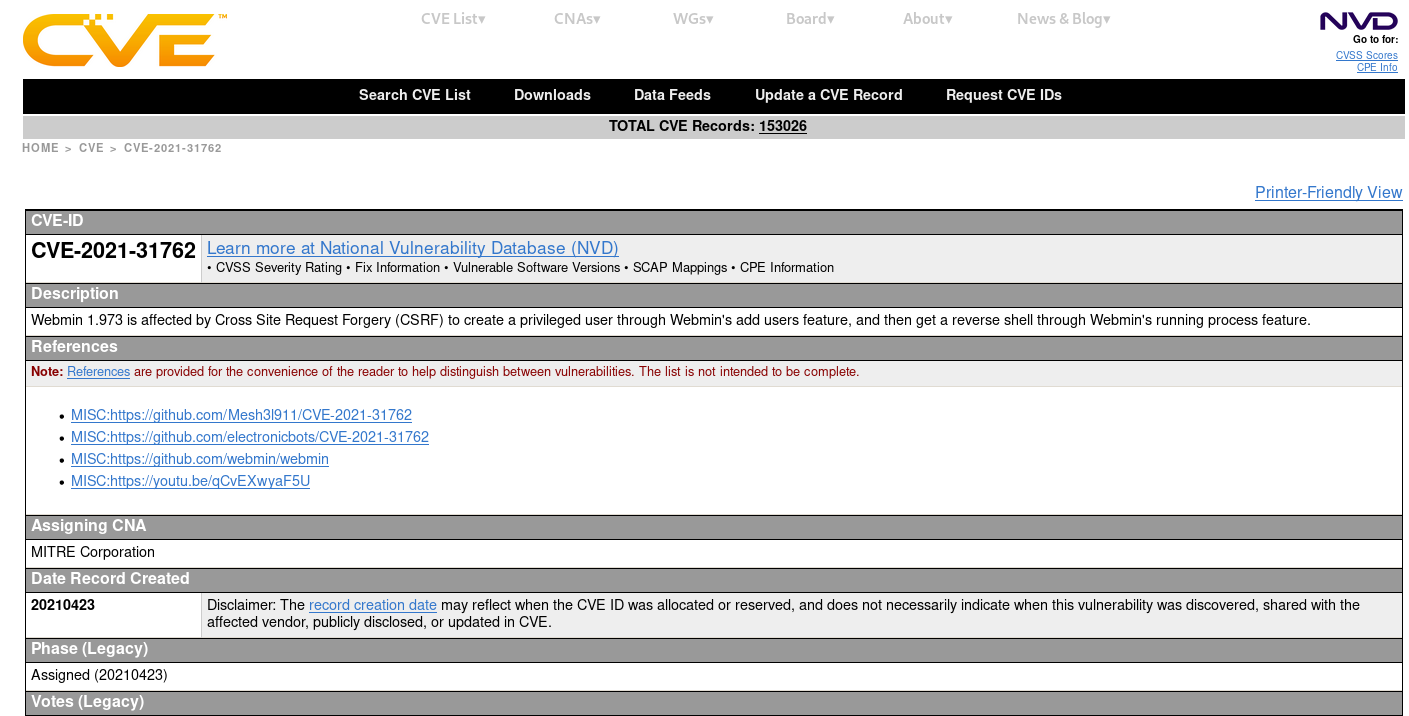
- CVE-2021-31762:
Webmin 1.973 - Exploiting a Cross-site request forgery (CSRF) attack to create a privileged user through the Webmin's add users feature then getting a reverse shell through the Webmin's running process feature
CVE-2021-31762
- CVE-2021-32156:
CVE-2021-32156
- CVE-2021-32157:
CVE-2021-32157
- CVE-2021-32158:
CVE-2021-32158
- CVE-2021-32159:
CVE-2021-32159
- CVE-2021-32160:
CVE-2021-32160
- CVE-2021-32161:
CVE-2021-32161
- CVE-2021-32162:
CVE-2021-32162
Acknowledgments
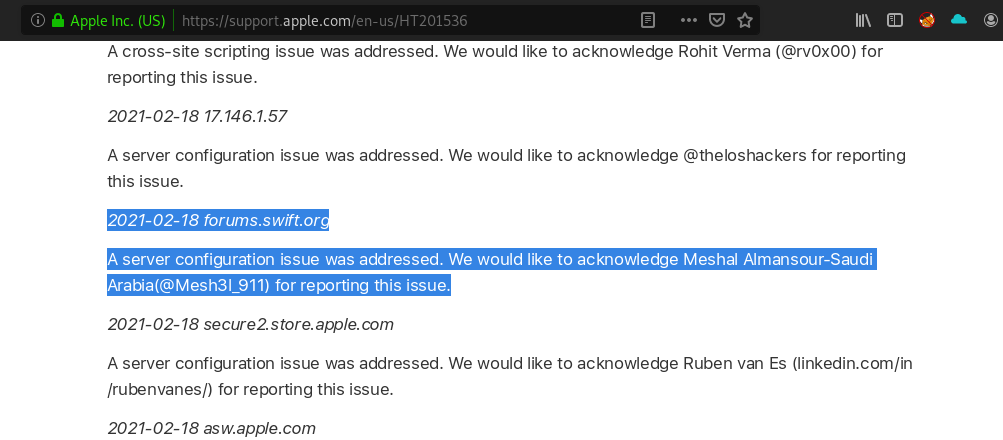
- Apple Hall Of Fame 2x times (Feb, 2023) & (Feb,2021):
Apple web server notifications (Feb, 2023)
Apple web server notifications (Feb,2021)
- Webmin Hall Of Fame:
Webmin's security alerts
- GE Healthcare Hall Of Fame:
GE Healthcare thanks page
- Shell Company:
Shell Company
- Ministry of National Guard:
Ministry of National Guard
- King Fahd University of Petroleum and Minerals:
KFUPM
Researches/Articles
- CVE-2024-25600 PoC:
0 click Pre-auth RCE in Bricks theme for WordPress [used by +25,000 websites]
CVE-2024-25600 PoC
- CVE-2023-3124 PoC:
0 click auth-RCE in Elemntor-Pro Plugin for WordPress [used by millions of websites]
CVE-2021-3138 PoC
- The story behind CVE-2023-4059:
The function wppb_create_form_pages that’s being hooked to the admin_init action is accessible to un-authenticated end-users due to the lack of proper authorization checks which allow threat actors to create/publish [Register/Edit Profile/Log in].
The story behind CVE-2023-4059
- Dependency Confusion:
In this Article I illustrated how we could done a supply chain attack through what's called Dependency Confusion attack [Dependencies, Package Manageers, Private/Public registries, DNS Exfiltration]
Dependency Confusion
- Debugging JS Based Web Apps Locally:
In this Article I introduced how debugging could be done using VSCode by debugging a basic NodeJS based app to illustriate different featers of VSCode
Debugging JS Based Web Apps Locally
- Auth Stored XSS Affects ALL Drupal Core Versions:
In this Article I demonestrated my latest finding in Drupal [Authenticated Stored XSS Affects All Drupal Core Versions] then [1-Triggering the vulnerability (Basic POC), 2-Uploading SVG File Using Python, 3-XSS to Bypaass the Anti-CSRF Token Using XMLHttpRequest (XHR), 4-Escalating Our Privilage to Administrator Using XMLHttpRequest (XHR)]
Auth Stored XSS Affects ALL Drupal Core Versions
- JSON Web Key Sets Spoofing (JWKS Spoofing):
In this Article I described [ What's JWK & JWKS?, jku Header, JWKS Spoofing Attack (Blackbox Approach), Challenge (Whitebox Approach).
JSON Web Key Sets Spoofing (JWKS Spoofing)
- Detailed Static/Dynamic analysis for(CVE-2022-21661):
In this Article my team and I approached the discovering/exploiting for the SQLi in the core of Wordpress (CVE-2022-21661) Statically/Dynamically using VS Code. We also wrote a custome plugin to do the 2nd part
Detailed Static/Dynamic analysis for(CVE-2022-21661)
- Infiltrating CS Beacon throughout different mediums [SMTP Server’s Banner, HTTP Response Header and DNS TxT Record]:
In this Article my team and I took a step towards an Infiltration technique that would make it a bit more complex to be detected.
Infiltrating CS Beacon throughout different mediums
- Out Of Band technique - DNS Exfiltration:
In this Article I illustrated [ Blind Command Injection ( White Box ), Blind Command Injection ( Black Box ), Out Of Band technique, DNS Exfiltration, Burb Collaborator, AWS ( EC2 , inbound rules ) +Godaddy, Tcpdump, Responder.py and Bind9 DNS Server ]
Out Of Band technique - DNS Exfiltration
- The journey from (.apk) to Account TakeOver:
In this Article I stated my jouney that endup with getting full acount TakeOver in android's app [ SSL Pinning Bypass > Network Traffic Analysis > Basic Dynamic Analysis(Genymotion, adb, Frida, Objection) > Basic Static Analysis( Jadx-GUI ) > Weak Encryption Algorithm > Password Generator(Crunch + Cusom Java script) > Account TakeOver ]
The journey from (.apk) to Account TakeOver
- Referrer Header Bypass > CSRF > Running Process endpoint > RCE > 0days > 3 CVEs > Webmin HOF:
In this Article we illustrated how did we approach our findings in Webmin
Webmin's Write-up
- Recon > Code Review > 0day > CVE-2021–3138 > Apple HOF:
In this Article I illustrated how did I approach my finding in Apple
Apple's Write-up
- Broken Links Hijacking ( BLH ):
In this topic I talked about chaining Sub domain TakeOver with External File Hijacking ( BLH attack ) to get XSS
Broken Links Hijacking
- DNS A record’s Subdomain TakeOver:
I saw alot of misconceptions about Sub-domains TakeOver and it's only about CNAME dns record so in this topic I did a POC in DNS A record’s Subdomain TakeOver
DNS A record’s Subdomain TakeOver
- BurSuite's Python environment and Rate limit bypass:
Here I talked about adding a python environment to the BurSuite by using jython then I talked about one way that might bypass the rate limit
BurSuite's Python environment and Rate limit bypass
- Creating Digital Ocean's droplet and x2goclient:
Creating Digital Ocean's droplet and then installing x2goclient to get a remote desktop
Creating Digital Ocean's droplet and x2goclient
- How one researcher got 37500 RS from Facebook:
I described here how one researcher was acknowledged by Facebook for finding SSRF
SSRF in Facebook
- Open Redirection escalations:
Multiple ways to escalate the Open Redirection vulnerabilities
Open Redirection escalations
- Local Route Poisoning:
Jmes Kittle introduced one type of host header injections which's Local Route Poisoning so What's Local Route Poisoning ? and how we can use it to bypass security checks such as Forbidden
Local Route Poisoning
- Python subprocess Module:
Getting Command Injection through python subprocess Module
Python subprocess Module command injection
PERSONAL PROJECTS:
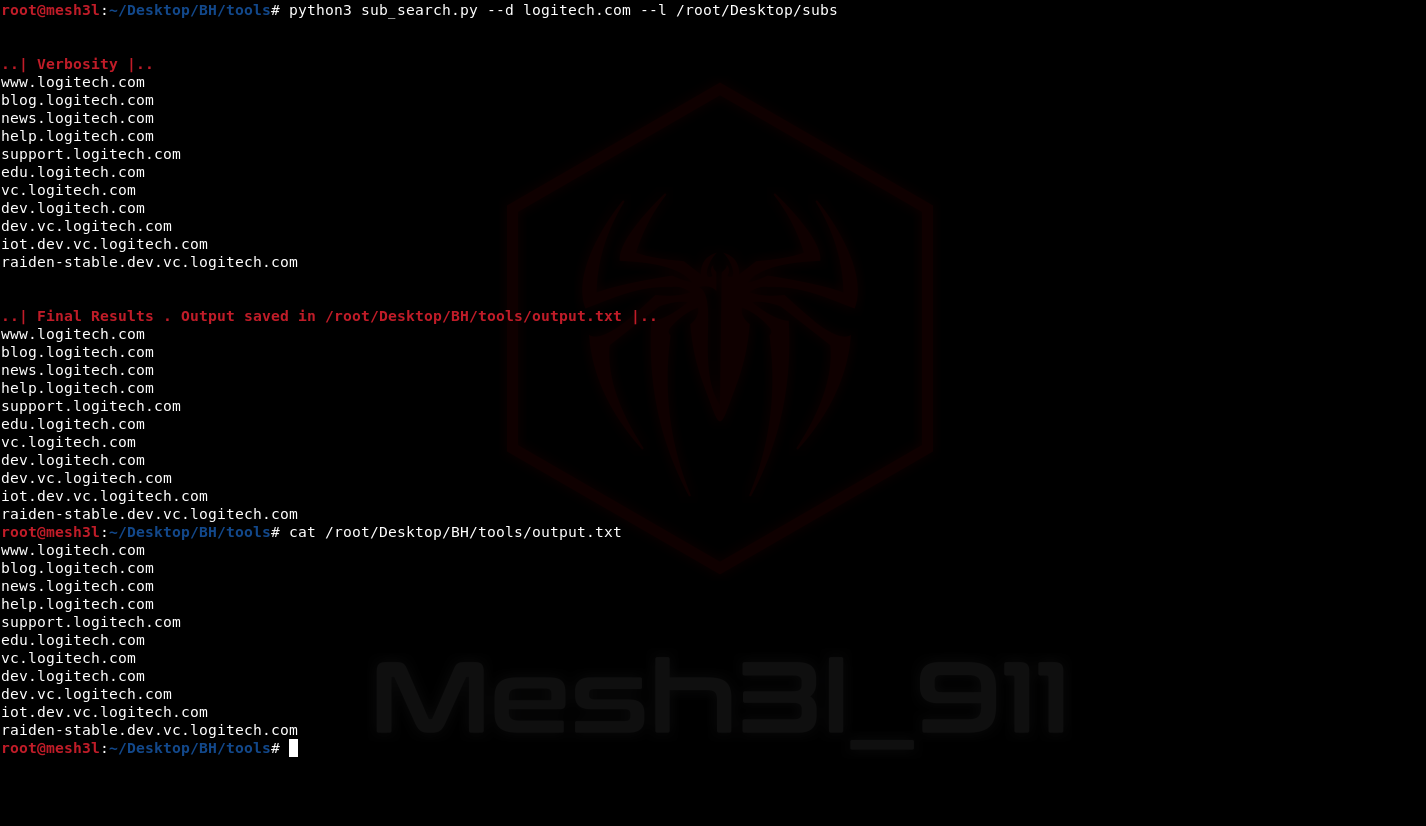
- Sub Search v1.0
A tool that automates the process of Getting all levels of subdomains that have A dns record by brute-forcing forward DNS lookup (recursively)
- Sub_Analyser v1.0
A tool that automates the process of testing web applications against Sub-Domain TakeOver vulnerabilities based on the CNAME DNS record
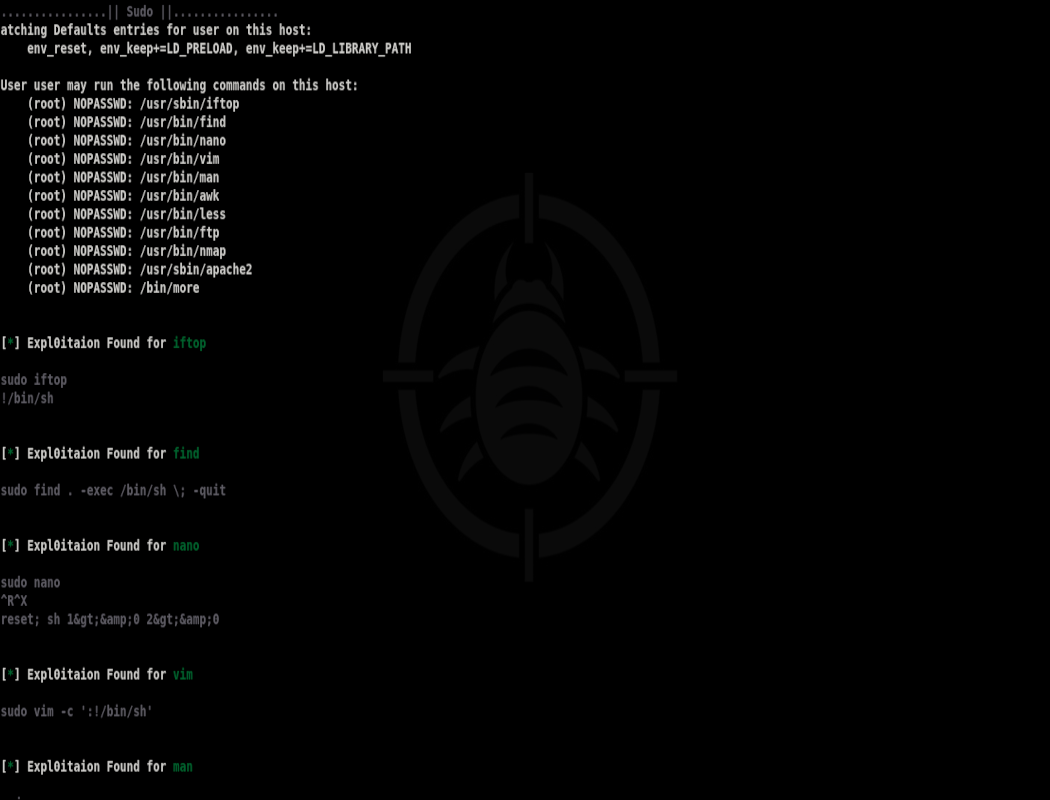
- Shell Escaper v1.0
A tool that automates the process of extracting the Shell Escape Sequences for Binaries with Setuid bit and Sudo out of GTFOBins with three different ways both locally and remotely
- Redirecter v1.0
A tool that automates the process of testing web applications against Open Redirection vulnerabilities
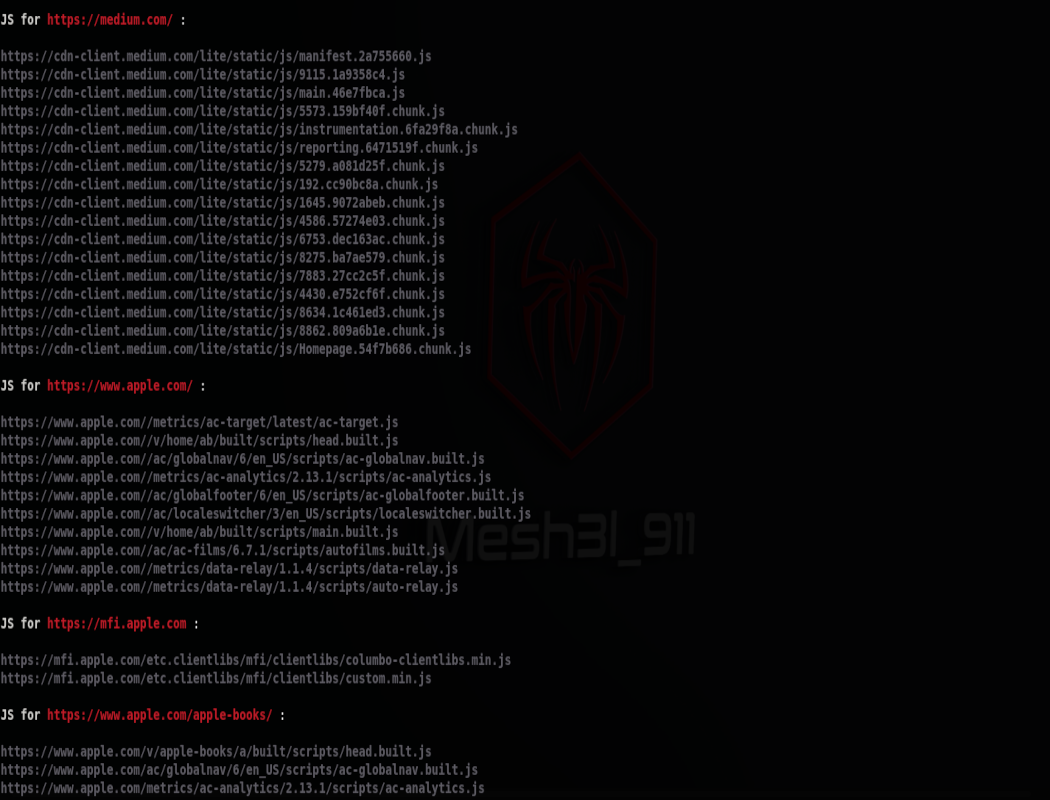
- JS Scrapper v1.0
A tool that automates the process of extracting JS files out of each URL provided within the provided urls list
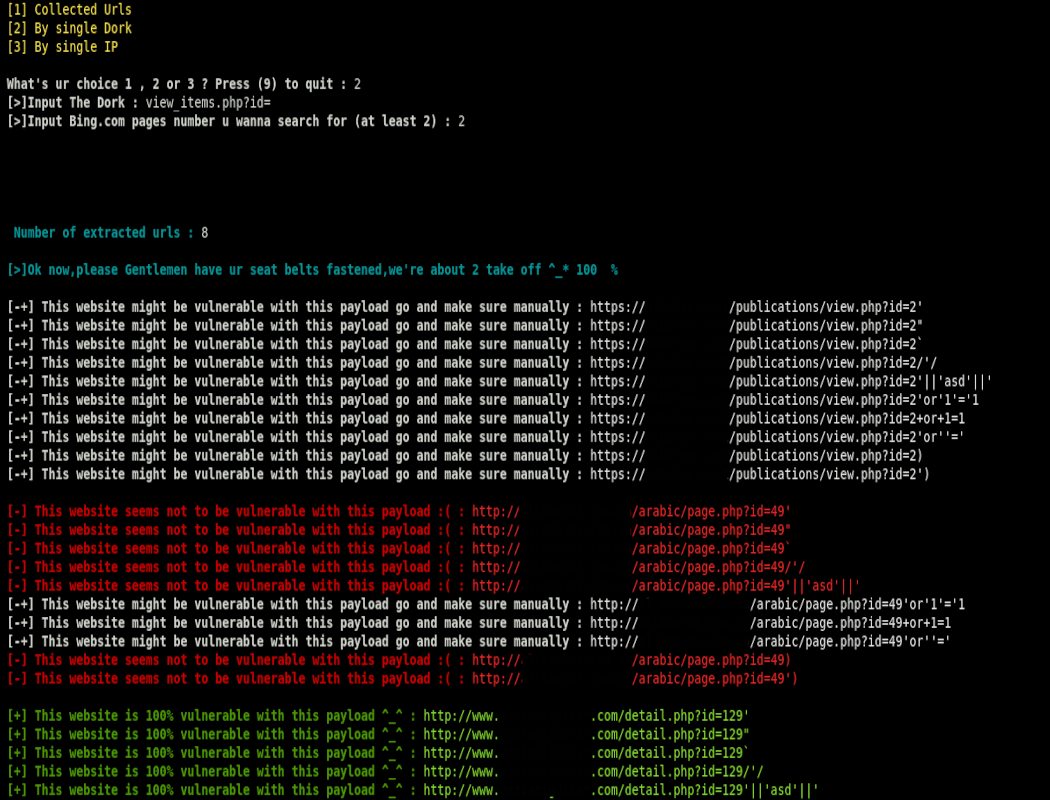
- SQLi_Checker v1.1
A tool to automate the process of testing web applications against different SQLi types > Get method > based on (known) payloads list with more features than SQLi_Checker v1.0 such as (Testing By IP , dork or collected urls ) & 4 Types of Blind SQLi
- SQLi_Checker v1.0
A tool to automate the process of testing web applications against different SQLi types > Get method > based on (known) payloads list
Competitions:
- First place ( 1st ) in Saudi Aramco CyberSecurity Chair 2021 with my team ( Potato )
Saudi Aramco CyberSecurity Chair CTF was to all cybersecurity students and recent graduates in SaudiArabia where 170 teams have participated from 41 different universities with a total of 807 compititors
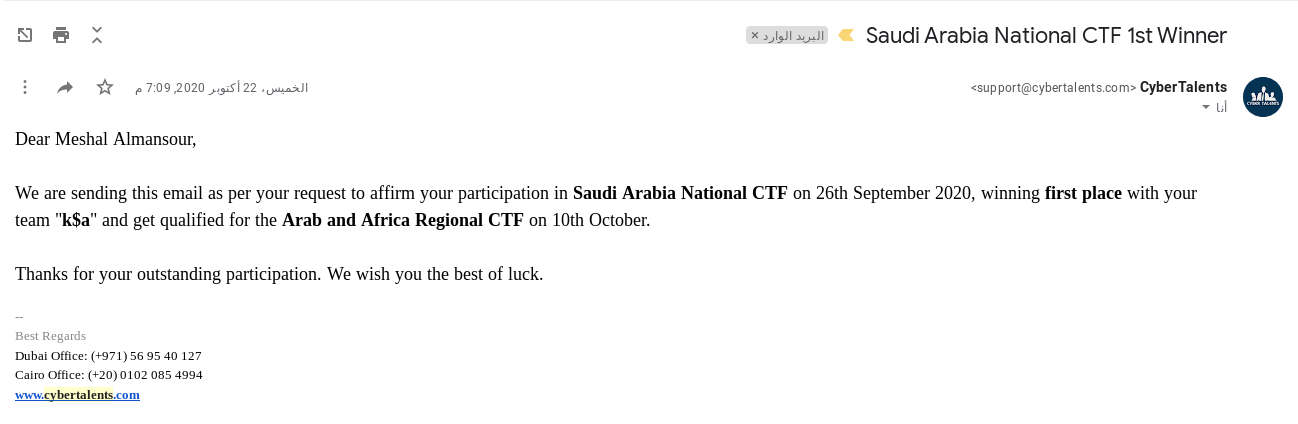
- First place ( 1st ) in CyberTalents Saudi Arabia National CTF in Finals with my team ( PeakyBlinders ) - 2021
Got qualified for the Arab and Africa Regional CTF ( among more than 25 countries)
- First place ( 1st ) in Watad CTF 2021 ( PeakyBlinders )
Watad's CTF was to all cybersecurity engineers & pentesters in SaudiArabia where 42 teams have participated with a total of 100+ compititors
- First place ( 1st ) in CyberTalents Saudi Arabia National CTF Qualification round 2020
Individually
- First place ( 1st ) in Cyber Hub universities CTF 2020 with my team ( BloodHunters )
Among ( more than 35 universities , 2000 students and 480 teams )
- First place ( 1st ) in Cyber Hub universities CTF 2021 with my team ( BloodHunters )
2nd version
- First place ( 1st ) in CyberTalents Saudi Arabia National CTF in Finals with my team (k$a)
Got qualified for the Arab and Africa Regional CTF ( among more than 20 countries )
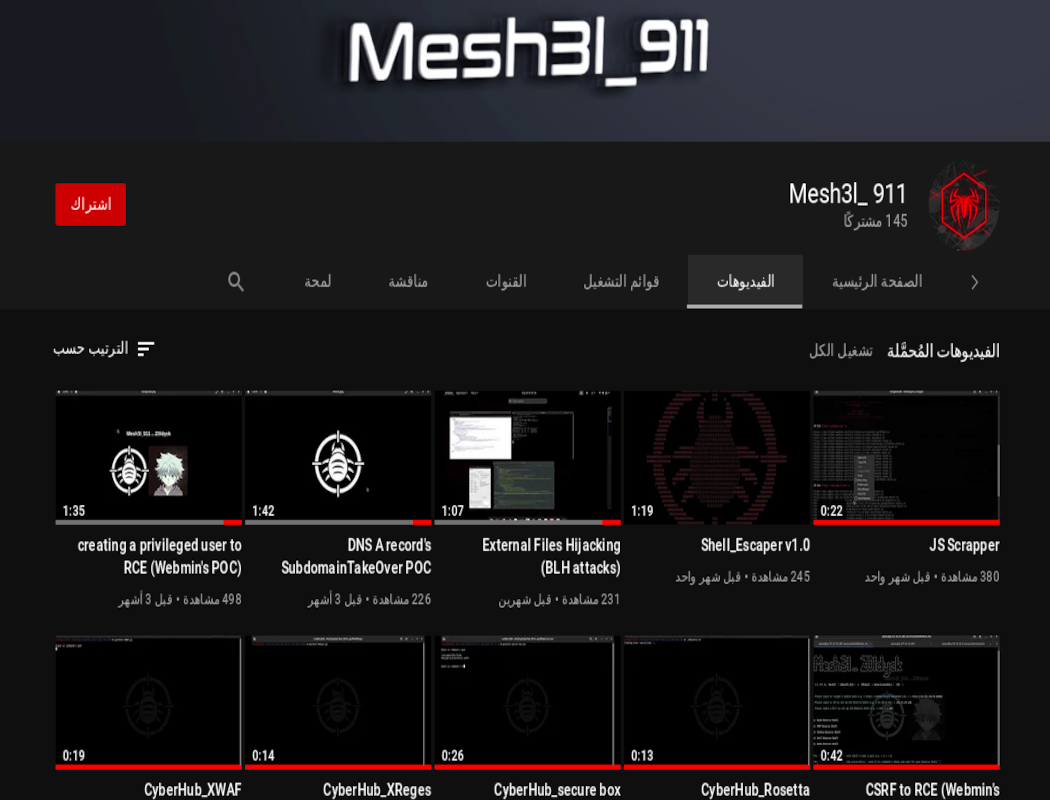
POCs & Automation
- Sub Search:
Sub Search
- JS Scrapper:
JS Scrapper
- Shell_Escaper v1.0:
Shell_Escaper v1.0
- DNS A record's SubdomainTakeOver POC:
DNS A record's SubdomainTakeOver
- External Files Hijacking (BLH attacks):
External Files Hijacking (BLH attacks)
- creating a privileged user to RCE (Webmin's POC):
Creating a privileged user to RCE (Webmin's POC)
- CSRF to RCE (Webmin's POC):
CSRF to RCE (Webmin's POC)
- CyberHub_Rosetta:
CyberHub_Rosetta
- CyberHub_secure box:
CyberHub_secure box
- CyberHub_XReges:
CyberHub_XReges
- CyberHub_XWAF:
CyberHub_XWAF
- CyberHub_backup:
CyberHub_backup
Accounts
Images













-ind.png)