
Agenda:
- Introduction (Story)
- Reconnaissance
- Finding (Source Code Review)
- Mitigation
- References
Introduction (Story):
One of my targets was a WordPress based web app, usually when I start testing such an app I do a common technique which’s looking for any vulnerable installed plugin that has a public exploit or at least a registered CVE so that I write the exploit myself. After struggling a bit, I found the thing that I was looking for and guess what? It was a remote command execution (RCE), Yesss we got the app right? Unfortunately not yet. The vulnerability was auth one while the target web app’s registration/login is CLOSED -_-. Eventually, I decided to move and look for something else that could be exploited w/o any authentication in place (un-auth).
Reconnaissance:
I’ve decided to fuzz the /wp-content/plugins/ dir so that I can detect/download installed plugins. I used a WP plugins list (multiple could be found in GitHub) then fired-up this command which simply will fuzz the dir using the list and download the plugin from https://downloads.wordpress.org/plugin/PLUGIN.zip if found.
1
while read -r plugin; do url="http://localhost/wordpress/wp-content/plugins/$plugin/"; wget --spider $url 2>&1 | grep -q '404 Not Found' || wget -nv "https://downloads.wordpress.org/plugin/$plugin.zip"; done < plugins.txt
Output: 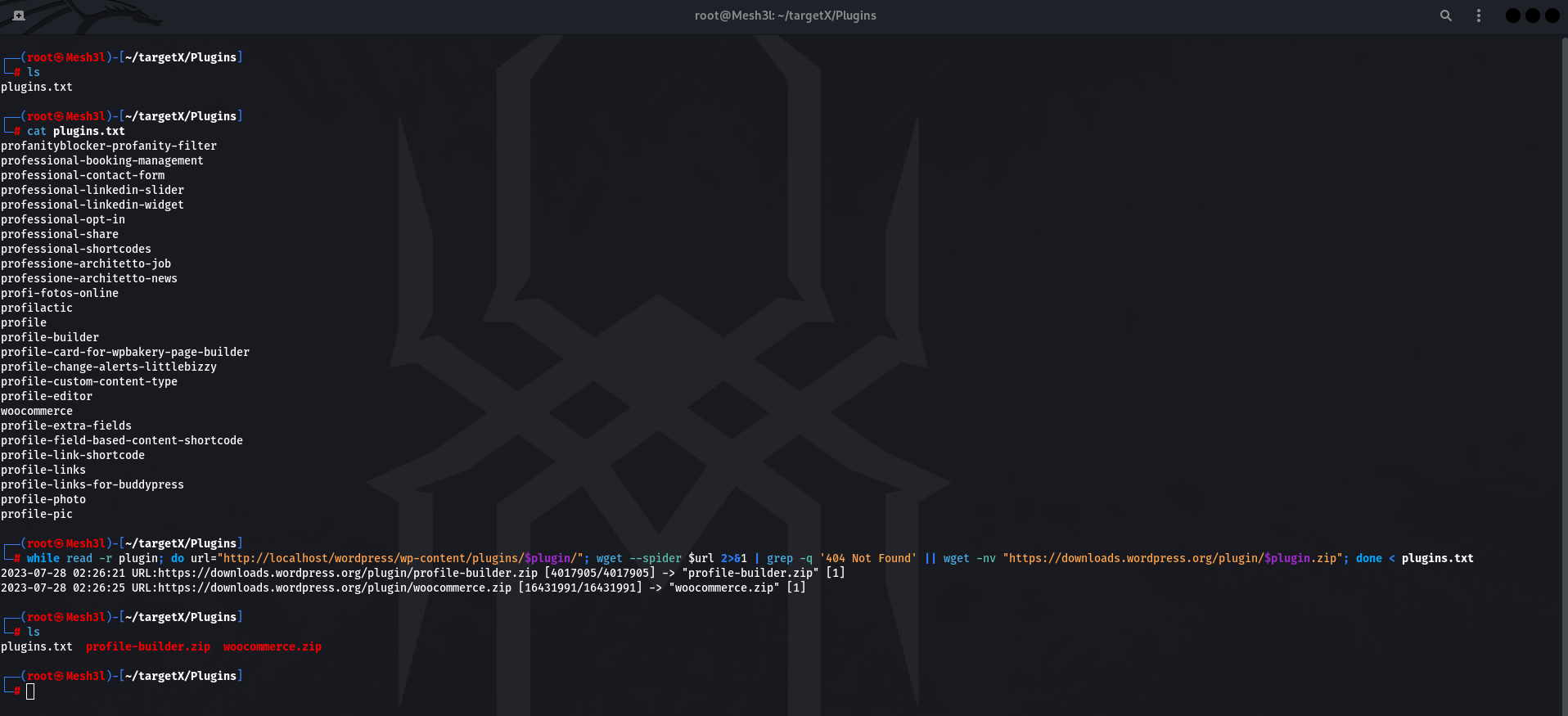
Now we are ready to dive …
Finding (Source Code Review):
Spent few hours reviewing the source code of some plugins which Profile-Builder was one of them (Profile-Builder is one of the popular free WP Plugins that has +60,000 Active installations https://wordpress.org/plugins/browse/popular/page/36/) and specifically this snippet of code cough my eyes.
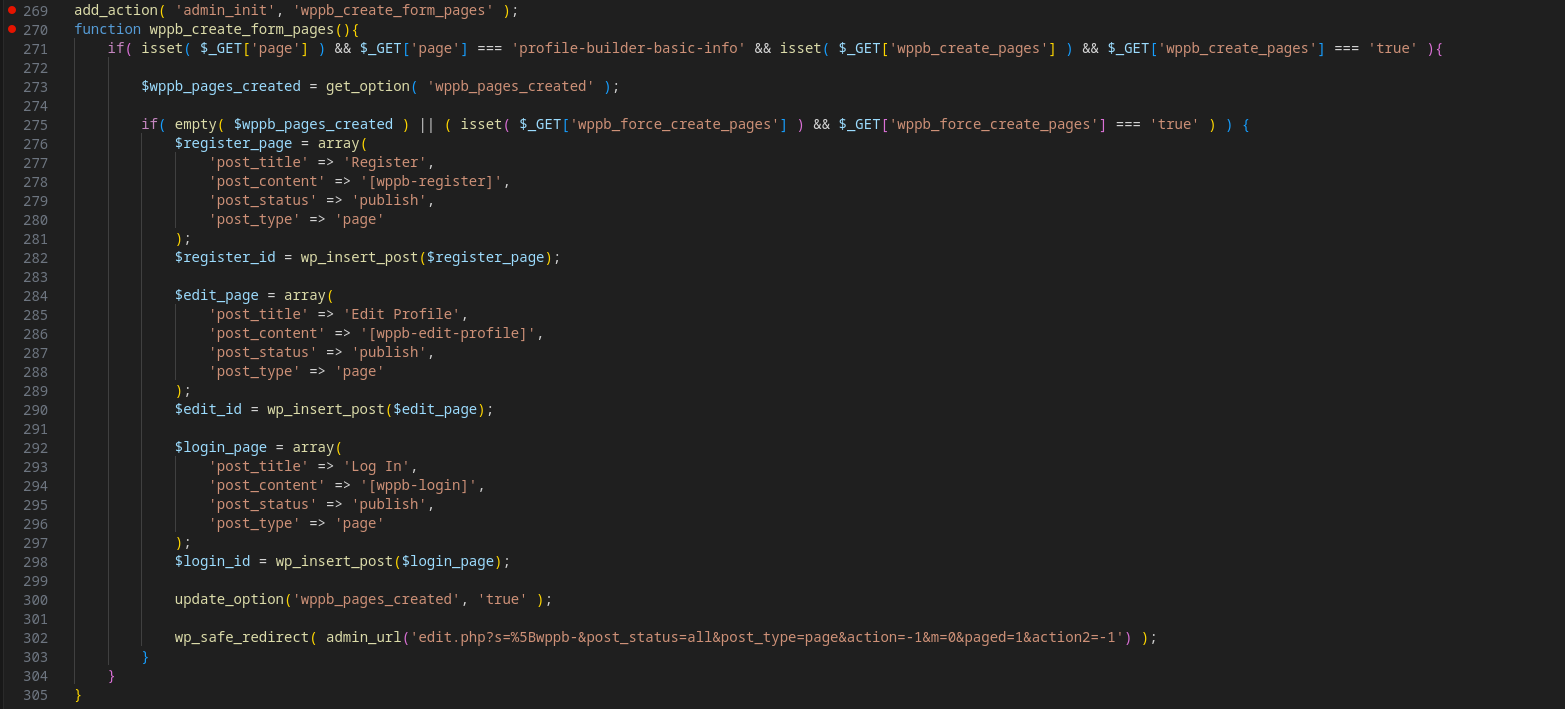
The function wppb_create_form_pages is responsible for creating form pages such as Register, Edit Profile and Log in and then publish ‘em. But wait a bit! It’s being hooked to the admin_init action and doesn’t have any sort of authorization checks!! Which means that I can craft a request which will then send the AJAX request to hit it and…? YOU GUESSED IT RIGHT. We can create/publish Register and Log in forms which means that we will be able to exploit that RCE we found earlier since we can register a new account and log in. This is exactly what I did in order to trigger that Auth-RCE ^_^.
Mitigation:
The mitigation could be done simply by adding a proper authorization checks such as current_user_can('administrator')
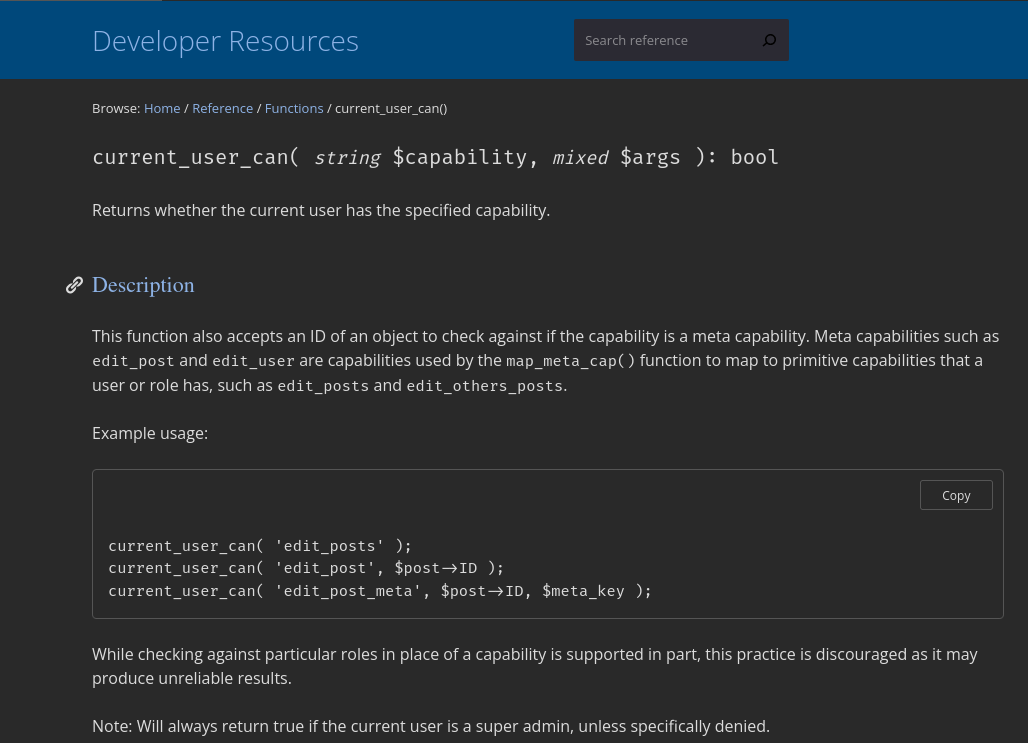
and this was part of the mitigation that was published by the team in version 3.9.8
Conclusion and References:
بالختام, دعواتكم لي ولوالدي ولمن أحب. وإذا أحد عنده إضافة أبد البلوق للجميع وأنا أول الشاكرين ^_^
- https://wpscan.com/vulnerability/fc719d12-2f58-4d1f-b696-0f937e706842
- https://wordpress.org/plugins/browse/popular/page/36/
- https://wordpress.org/plugins/profile-builder/
- https://developer.wordpress.org/reference/functions/current_user_can/
- https://wpscan.com/